Managed Intrusion Detection
HOW IT WORKS?
 RT Ducks are devices that sit in your network waiting for someone to access them without authorization and alert you as soon as it happens, in the cyber security industry these devices are known as Honeypots.
RT Ducks are devices that sit in your network waiting for someone to access them without authorization and alert you as soon as it happens, in the cyber security industry these devices are known as Honeypots.
We will configure and deploy Ducks throughout your network (these can be hardware, virtual or cloud-based birds!). Each duck can pretend to be a Windows file server, a router, web servers or basically any other device that can grab the attention of an ill actor. Each one hosts realistic services and looks and acts like its namesake.
Attackers prowling a target network look for juicy content. They scan and explore the network looking for unsecured file servers and gain access to documents and any other data they can hold ransom.
This is where the RT Ducks come into play, they will sit there, acting as an unsecured device that will tempt the attacker, and as soon as they access any of the fake content stored in the Duck the device will trigger a notification of the event with identifying data like the IP address of the attacker.
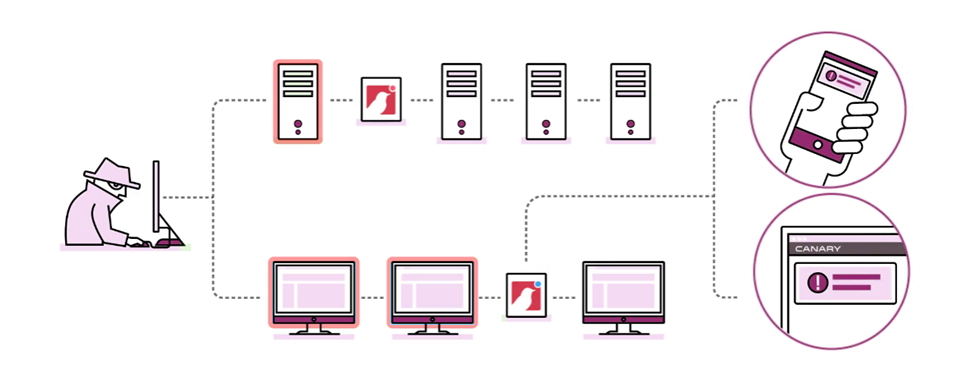
MANAGED SOLUTION
We manage all the ducks for our customers ensuring they are checking in and working correctly.
Your RT Ducks constantly report in, and provide an up-to-the-minute report on their status, but this doesn’t need to become another pane of glass that you need to constantly monitor. Even customers with hundreds of Ducks receive just a handful of events per year. When an incident occurs, we alert you via email, text message, slack notification, webhook or syslog.
FREquently ased questions
Isn’t this Just a Honeypot?
Yes and No.
Honeypots are a great idea. Everyone knows this, so why is almost nobody running them on internal networks? Simple: because with all the network problems we have, nobody needs one more machine to administer and worry about. We know the benefits that honeypots can bring but the cost and effort of deployment always drops honeypots to the bottom of the list of things to do.
Ducks are plug and play, they can be deployed in minutes (even on complex networks), giving you all of the benefits without the admin downsides.
How easily can they be deployed?
It usually takes less than 15 minutes to have our Duck ready for action on your network. With just a few clicks, you’ll have a high interaction honeypot, and be able to track who’s browsing shares for PDF documents, trying to log into a NAS, or port scanning your network. We can also send the devices to you preconfigured.
How do they communicate with the console?
Ducks are deployed inside your network and communicate with the hosted console through DNS. This means the only network access your Duck needs is to a DNS server that’s capable of external queries, which is much less work than configuring border firewall rules for each device.
Ok. You have 2 minutes, how does this work?
Simply choose a profile for the Duck device (such as a Windows box, brand name router, or Linux server). If you want, you can further tweak the services your Duck runs.
Perhaps you would like a specific type and version of a server like IIS or FTP, or a Windows file share with real files constructed according to your own naming scheme (say, 2016-tenders.xls).
And that’s it. Attackers who have breached your network, malicious insiders and other adversaries will make themselves known by accessing your Duck. There’s little room for doubt. If someone browses a file share and opens a sensitive-looking document on your Duck you’ll immediately be alerted to the problem.
You possibly already do have a problem, you might just not know it. An RT Duck changes that.
So Ducks are sensors. Do you use them to do machine learning for anomaly detection?
No. Duck doesn’t do anomaly detection (with machine learning or otherwise) by learning to detect malicious behavior in day-to-day activity. The Duck triggers are incontrovertibly simple: if someone is accessing your lure-files, or brute-forcing your fake internal ssh server, then you know you have a problem. Duck uses deceptively simple, but high-quality markers of trouble on your network.
What if an attacker DoS’es the device or compromises it?
If your Duck can get off just one alert (and it really should) then your console far away is going to log and alert on this. Whatever happens to the Duck after that won’t matter since it stores nothing of value.
What if an attacker identifies the device as a Duck? Won’t they simply avoid it?
Identification will require active interrogation of the devices, and we detect common methods for fingerprinting then alert. After that, even if the attacker correctly identifies a Duck, you know they’re looking and can investigate further.
